Setting up your web server with an SSL certificate is now easier than ever. Not only does it make accessing your website more secure by encrypting the data transferred via an HTTPS connection but Google also now factors it into your site rankings. This guide will show you how to configure HSTS header with ease via Cloudflare.
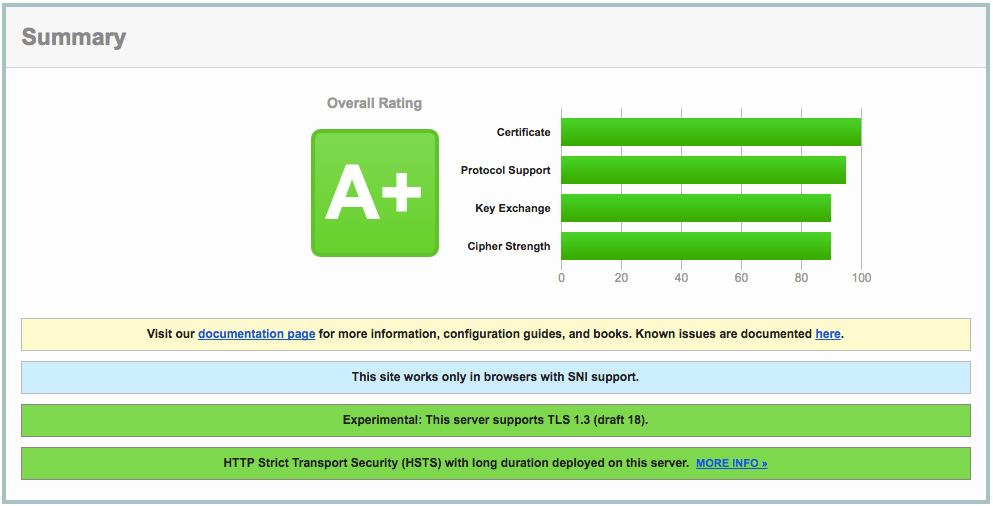
If you are not too sure how secure your website is, try testing it here:
https://www.ssllabs.com/ssltest
It will fully analyse your SSL configuration and give you a score and a full report. Quite often it will come back with a score of 'A'... which sounds pretty good but you are still potentially exposed to a Man In The Middle (MITM) attack against the server, decrypting previously captured data, or in the case of client initiated SSL renegotiation, cause a denial of service against the server.
SSL configurations are considered insecure if a server supports one or more of the following:
- Connections without Strict-Transport-Security set
- Connections with forward secrecy disabled
Not happy with your 'A' now? Read on how to hit that A+ and keep your parents... I mean your boss happy.
How to get an A+ on your SSL report - configure HSTS!
You could run the test and then try and manually configure everything yourself on your server... but unless your a super nerd and know what you're doing, you will most likely waste a lot of time going around in circles or finding out that the server or service you are using does not allow or support HSTS.
Cloudflare to the rescue!
Cloudflare makes it super easy to configure HSTS and SSL settings with a few clicks. Once you have installed Cloudflare on your domain follow these steps:
1) Ensure the orange cloud is enabled on the DNS records you want to secure:

2) Configure at a minimum "Flexible SSL".
If you have installed a proper certificate on your web server you should use "Full SSL" under the Crypto settings area. (You might need to wait a few hours for it activate)

3) Make sure you website is setup to run over HTTPS
This step is important as not all websites play nicely. You might need to get your web developers to tweak some settings (or contact us if you need a hand).
To find out if your website will run over SSL, simply replace 'http://your-website.com' with 'https://your-website.com' in your browser. Then surf around all the areas of your website and ensure you do not get any mixed content errors, and that all images / scripts are working as they normally do (every time a page loads check that the browser is still using HTTPS, many CMS or frameworks will often redirect to the non secure version on form submits or even page loads).
If everything is working as expected you should force all traffic to run over HTTPS. This can be done many ways - but again Cloudflare makes this easy:

You can also use Cloudflare Page rules to achieve this if you do not want all subdomains / other DNS records to use HTTPS.
Once you have enabled this, test again to ensure everything is redirecting and working as expected.
4) Enable HTTP Strict Transport Security (HSTS)
Important! Do not continue if you had any issues with step 3 - make sure you resolve those issues first. It could result in your website becoming inaccessible for users. This setting will be cached on visitors browser for 6 months if the site is not running on SSL and they visit it will trigger an error in their browser. Basically your website from now on has to run over the secure link.

Now run your test again on https://www.ssllabs.com/ssltest and behold your A+ score!

5) Extra credit
Cloudflare has a few other SSL settings. I would also recommend turning on:
- Require Modern TLS (This can be an issue for older browsers)
- Opportunistic Encryption
- TLS 1.3